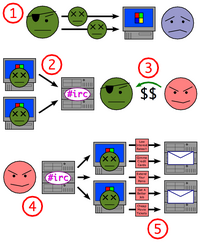
Be careful to Malicious Commands in Ubuntu
Users in Ubuntu (UNIX) use a lot the Terminal window to run different commands. But some of this commands can be extremely dangerous for you system. From these commands your files can be deleted, a huge number of processes can…