Enhance Linux Server Security #2 – Install ModSecurity
This is very short video tutorial but important for you web server security. Install ModSecurity is very easy and will take you just a few minutes.

This is very short video tutorial but important for you web server security. Install ModSecurity is very easy and will take you just a few minutes.
Ankit Fadia is an internationally renowned independent computer security consultant who has authored several internationally best-selling books on Computer Security. Want to become an Ankit Fadia Certified Ethical Hacker? The BBC says at 14 years of age, Ankit Fadia defaced…
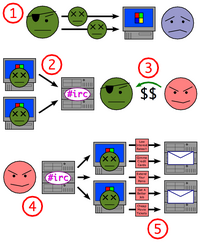
Botnet is a jargon term for a collection of software robots, or bots, which run autonomously and automatically. They run on groups of "zombie" computers controlled remotely by crackers. This can also refer to the network of computers using distributed…
Exclusive by Wired.com Promises of Hollywood fame and fortune persuaded a young hacker to betray former associates in the BitTorrent scene to Tinseltown’s anti-piracy lobby, according to the hacker. In an exclusive interview with Wired News, gun-for-hire hacker Robert Anderson…

Hackers have newer methods to hack into your systems.They are smart enough to detect security loop holes in your PC and enter through open ports,unencrypted Wi-Fi connections,malicious websites or internet servers.It is better you check your PC periodically for invasions…

Two weeks to the day after Apple’s iPhone software update wiped third-party applications from the device and disabled unlocked phones, the hackers have struck back. The Unofficial Apple Weblog posted details of the iPhone Dev Team’s latest effort, which once…

Writing and using Free software is not just a programming, is a kind of philosophy. While programming language is all you need to program, this article is about how to join the community, get friends, do a great work together…