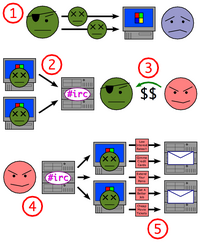
eLearning – What is a Spyware?

Spyware is computer software that is installed surreptitiously on a personal computer to intercept or take partial control over the user’s interaction with the computer, without the user’s informed consent. While the term spyware suggests software that secretly monitors the…